SSL Considered Harmful
A page on my various security writings.
Each of the controversial issues raised herein
is an advanced attack on a security system.
Still, each is written for accessibility in mind - any
developer or manager within the general rubric of security
should be able to follow along. If not, please complain!
"the survival value of intelligence is that it
allows us to extinct a bad idea,
before the idea extincts us"
or, alternate translation:
"The scientist can annihilate his theory by his critique,
without perishing along with it.
In science, we let our hypotheses die in our stead."
Karl Popper
[1]
Originally, this was a collection of rants
designed to reverse-engineer SSL, certificates
and the wider system of secure browsing.
The mission has somewhat migrated to a more
general one of improving our understanding
of security systems
(both mine and anyone else who wants to read as well).
But, please note:
When I first started this debate, it was just a bit
of fun, a way for a security guy to look at a
system afresh, and stretch the mental muscles.
Since then, however, phishing and the rest
emerged as serious Internet fraud, and provided
a benchmark and a reality to security that wasn't there earlier.
It all became very serious.
Hard Truths about the Hard Business of finding Hard Random Numbers
AS many have noticed, there is now a permathread (Paul's term) on how to do random numbers. It's always been warm. Now the arguments are on solid simmer, raging on half a dozen cryptogroups, all thanks to the NSA and their infamous breach of NIST, American industry, mom's apple pie and the privacy of all things from Sunday school to Angry Birds.

Yet we've come to a point I believe where we do know enough. This is my attempt to establish a minimum practice for building RNGs, in 12 points.
Originally posted on FC, the updated copy now lives here. Read on for the Hard Truths about the Hard Business of finding Hard Random Numbers...
Why the NSA loves the one-security-model HTTPS fanaticism of the Internet
OF all the things I have written about the traps in the HTTPS model for security, this one diagram lays it out so well, I'm left in the dirt. ...
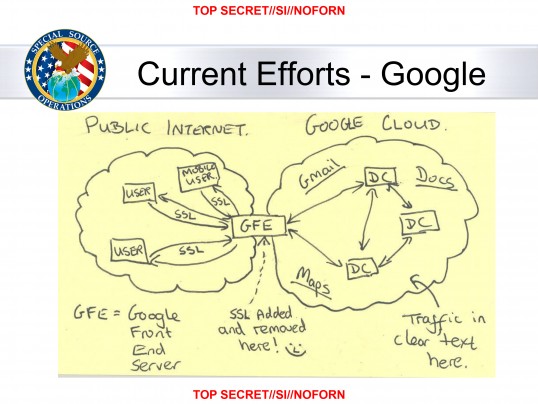
Read on for Why the NSA loves HTTPS...
History of Risks & Threat Events to CAs and PKI
IN Risk Management terms, History refers to the series of attack events that are documented and examinable, for the purpose of validating threat attack models.
This is an ongoing effort to document those events that have been reasonably seen as attacks and threats relevant to the CA and the usage of certificates. The purpose of this page is to help risk assessments validate their threat models against recorded events.
Read on for History of Risks & Threat Events...
The Curse of Cryptographic Numerology
The problem of cryptographic numerology has plagued modern cryptography throughout most of its life. The basic concept is that as long as your encryption keys are at least "this big," you're fine, even if none of the surrounding infrastructure benefits from that size or even works at all. The application of cryptographic numerology conveniently directs attention from the difficult to the trivial, because choosing a key size is fantastically easy, whereas making the crypto work effectively is really hard.
Read on for the Curse of Cryptographic Numerology...
What makes a Security Project?
This is a (three years) old essay in which I looked
at as many projects as I knew at the time, and
compared them.
Out of the comparison, I developed a list of 20
simple measures or binary metrics with
which to rate them.
Mapped as a matrix and totalled up for top scorers,
the ideas may be useful for others to read.
It might also be amusing; the lowest scorer of
all is my all time favourite crypto application.
Note the work is unfinished and not something
I suggest you rely on. I offer it more as a source of
debate and usefulness to others, and please excuse
the bountiful errors.
Adverse and other comments on the blog, please!
Hypotheses in Secure Protocol Design
How to create a secure protocol?
Or a secure product of any description?
It's a vexing question, and many have broken their spirits on it.
Over time, threads and rhymes emerge,
and these I've collected into a series of hypotheses.
I am slowly introducing them over on the blog,
as some topical news develops to introduce the point.
So far, I've got as far as H3 and H6:
White Helicoptor
-
Is eavesdropping a "Clear and Present Danger"
-
the definition of a validated threat?
In which I define a validated threat as one which is
a Clear and Present Danger.
Compared and contrasted with the emerging threat of
eavesdropping, I conclude that it is Present and a Danger,
but is not yet Clear.
Reliable Connections are Not
Perhaps better entitled "On the limits of reliability in connections."
This is a rant that documents the specific corner cases that
make connections "mostly reliable."
For the most part, most software engineering does not need to
worry about these nitpicking details.
Connections are reliable enough, they are
"good enough for government work"
as the saying goes.
But for those few applications that require real reliability
- finance, payments, medical, weapons, robotics, transport, etc etc -
something else is needed.
(Well, maybe that isn't such a short list after all?)
This essay lays the groundwork for that something else.
That might come later, in time. If you really truly
require it though, you can always reliably pay for it :)
(Comments can go here.)
Voice Threat Models are Snafu
A recent spate of reports on VoIP and cryptophones has called
for more encryption. I fear that we've bungled the threat
model yet again - in exactly the same way as with SSL.
Cryptography is the art of using mathematics to protect things that
we know we can protect with mathematics; unfortunately the desire
to throw bucketloads of cipher bits at the problem has missed the
fact that by far the biggest risk to users of phones is *tracking*.
(More:
-2
-1
1 2.
)
Security Revisionism
Not really a rant, but an article for
JIBC
that assumes security is failed,
and surveys open areas of research to help:
Abstract.
Security isn't working, and some of us are turning to
economics to address why this is so. Agency theory casts
light on cases such as Choicepoint and Lopez . An economics
approach also sheds light on what security really is, and
social scientists may be able to help us build it.
Institutional economics suggests that the very lack of
information may lead to results that only appear to speak
of security.
The State of the Net - 2006
-
Rant out the Old, rant in the New!
Another year has passed, and what was the big news?
2005 was ....
The Year I Lost My Identity.
2006 I christened as
The Year of the Bull
with a fine representation from
Daniel Kozan.
GP4.3: Case Study #3 - Phishing
As an outgrowth of a rant or essay on the economic interactions
of fraud and security in new business models, I wrote a case
study on Phishing. For the most part, the value of this
case study is the listing of Forces imposing on SSL's
development around 1994-95. This approach draws from Porter's
Five Forces approach to institutions. It's a fun list,
even if it has roots back into b-speak.
The wider point I'm making in that case study is that the
SSL and certificates system was put in too early, before GP.
To see what that means, you'd have to read through the three
core sections:
The wider concept of when to put the security system in
came out of many analysies, including that of SSL as presented
in these rants. It's probably worth mentioning that we made
the same mistake with Ricardo. The key observation drawn
from these experiences was that security that
came in late seemed to work better than security that came in
early - why was that? That's what the rant tries to answer.
Security Usability (PDF only)
The security industry's desire for no-risk
security has resulted in less security overall.
Frankly, if people don't use it, it doesn't deliver
any security whatsoever, so usability has to come
first.
I'm not so sure what's so hard to get about this
concept, but security experts continue to suck
air in between the teeth when they hear of encrypted
email without proper certificates or VoIP applications
without Guild-approved cryptosystems.
So this battle has only just begun it seems.
The article was co-written with
Peter Gutmann
for the Crypto Corner of IEEE's
Security & Privacy magazine (and is copyright by them).
It also marks my first serious use of wikis
which in itself was quite enlightening.
Phishing
-
what it is and how it will eventually be dealt with
When
JIBC
asked me after a 9 year absence to write a
2 pager on the one subject that is more important than
any other, it took no more than nano-seconds to leap onto
my hobby horse - Phishing!
In two pages I could do no more than present an
overview for business and financial executives.
As a summary of my thoughts as to the state of the
art in how to address phishing, it's pretty good.
Where it stops short of course is doing the work.
That issue is the subject of future rants and articles,
as these days there is more interest in the meta-topic
of security practice than phishing per se.
"For a successful technology, reality must take
precedence over public relations, for nature cannot be fooled."
Richard Feynman
[2]
A Blackbird Moment
-
Microsoft confirms phishing is an attack on the browser
The crusade over browsers and phishing has become an underground
legend that nobody dares name. Yet, when security professionals
hear the name, they know the site!
Infamy carries its costs though - both to my own reputation
and to the reputation of browsing itself.
So it was with some degree of personal relief that we now
have, as an industry, focussed the browser manufacturers on
the goal. Phishing is an attack on the browser, and there
is no longer a need for us to discuss that.
Thanks, Bill.
The Goal of Security
(Security Signalling - III)
Adam's insightful question on 'security signals' caused
create ponderment. It's a really tough one. One thing
that stuck in my mind was that FreeBSD and OpenBSD are
secure. The rest? Don't know.
So why are these two, and presumably other BSD variants
like BSDI and NetBSD, so stuck in the mind as 'secure' ?
What's the signal?
Here's one answer - these two operating systems practice
the Goal of Security.
It is partly in their writings but more importantly it is in their
actions.
This essay attempts to lay out what it means to subscribe
to Security as a Goal. It is nominally aimed at another
project, Mozilla, which is rapidly approaching a test of
its maturity and security. As it grows without apparent
limit, it seems destined to enter that love-it-hate-it
area where the user base is too big for attackers to ignore.
Mozilla may well claim to be
passionate about security,
but those are just words. In actions, Mozilla have had it
easy; no real attacks in living memory
(Shmoo was not an attack but an exploit),
unlike the BSDs which
have had to take the brunt of hacking attacks since
the dawn of time. Time to get some security into the blood.
Netcraft breaks ranks and points the crooked black claw of doom at the SSL security model
The debate on SSL's security model just gets better and better.
Now Netcraft have turned the whole model on its head,
and created a browser plugin (for IE only unfortunately)
that does the security thing by reference to a centralised
database.
Who'd a thunk it?
User education: worse than useless
I didn't realise it at first, but this was a question
that seriously needed an answer. Just why is it that
we've spent the last decade giving the user good advice
- the padlock protects you, beware of 40 bit crypto,
or don't click on that email link - and we're still in
this security mess?
"I think the subject which will be of most
importance politically is Mass Psychology...
Its importance has been enormously increased
by the growth of modern methods of propaganda...
Although this science will be diligently studied,
it will be rigidly confined to the governing class.
The populace will not be allowed to know how its
convictions were generated." ---Bertrand Russell
As with most complex things, the answer is so simple we
probably walked right past it:
the users don't pay attention to education, and for quite
good reasons. Which results that more user education is
dangerous, as it avoids facing up to the real problem.
The State of the Net - 2005
-
in several rants around our new year of 2005,
leading to the future, year by year...
Yes, it's been more than a year now, and little progress
has been made.
Other than by phishers, that is, so I christened 2004 as
The Year of the Phish.
Of course, we all knew that, so the more interesting future is
in 2005, which I have christened as
The Year of the Snail.
Under pressure, and deprived of caffeine, I also wrote
2006, and beyond...
but I wasn't able to christen that far ahead.
Still, the Year of the Dogs is one contender, as I predict finally in
Identity Theft: Why Hollywood has to take one for the team.
Sucking on the Lemon
(Security Signalling - I)
Adam Shostack pointed out how
signalling is a lemon
in its own right in the security industry, which got me thinking.
Here's my proposal for a good signal:
report all your crack attempts on a daily
basis, and watch what happens when you actually get hacked.
Just like sucking on a lemon, this will reveal to the market
how secure your stuff is, whatever you do with the lemon
that suddenly went sour!
The Market for Lemmings
(Security Signalling - II)
Again following
Adam's lead,
I've added an effort to
define some characteristics of the security market.
In brief: the security product is one that defies testing.
I'm not sure that this is a new observation, but we have to start
by documenting what we do know...
VeriSign's conflict of interest creates new threat
VeriSign are the market dominating seller of CA-signed certificates
to help you in "secure ecommerce." What is less well known is that
they are also a leading facilitator of
"lawful interception and subpoena requests"
services to Law Enforcement Agencies, ISPs and telcos!
Can you say conflict of interest ??
New Attack on Secure Browsing
Just when you thought it was safe to get back into browsing...
I stumbled across this new way of futzing with people's minds.
This page is now protected - see the
 padlock up on the top left of the URL bar.
padlock up on the top left of the URL bar.
Microsoft Internet Explorer users - secure browsing is not available
to you as your browser is full of spyware, trojans and other malware.
You should
download
and install
Firefox
this instant ! ! !
Alternatively, you can get more placebo security by adding this page
as a Favourite, and then you will see what this attack is all about.
Making VeriSign like CocaCola
-
How CA Branding works against Phishing, substitute CA attack, etc etc
I've been proposing the branding box for some time now,
but for some reason, this powerful idea to solve one of
the great MITM attacks on SSL secure browsing hasn't
gained traction. Here's an explanation of how branding
can segment the MITM into 4 spaces, and clearly designate
who is responsible for protection in that space.
The really exciting news is that Amir and Ahmad are
actually
building this into Mozilla.
What we do in the security world is we pick a system,
and we tear it apart. It's a way of preparing to build
the next system, and it's also fun.
It has been known for a long time that secure browsing
was only secure by dictat, but it didn't really matter
as nobody ever got hurt. Ideal system to pick apart,
and that's what this page is about.
Since then, however, phishing has arisen as
perhaps the first serious fraud that is totally
Internet only. My best
estimate of losses so far
- a number that is very hard to quantify - is about one billion dollars.
"Science is the best defense against believing what we want to."
Ian Stewart
[3]
Hence, my next rant:
Question on the state of the security industry
Phishing has become very serious. What is equally serious
is that the Internet security community that put secure
browsing in place back in 1994-1995 is ignoring it,
all the while as the maelstrom grows around it. Meanwhile,
there are consortia being formed, headlines being written,
politicians bailing in, and identity theft is now
the number one US consumer problem. Still ... nothing.
What's going on?
Who are you?
(WYTM revisited)
In contrast to the below, here
is a rant that argues that WYTM may not be an appropriate
question for a system like secure browsing. Although argued
for email, the analogy holds: If we can't
identify who the users are, adequately, then we can't
identify their threats. Oops! Yet more evidence that
Mallory was misrepresented as a threat...
Dr. Self-signed
or
How CAs Learned to Stop Worrying and Love the Cert?
Why is the market for certs so moribund? Well, one reason is
that it lacks discrimination - a critical component as all
marketeers know. This essential ingredient can be added
easily with a dose of self-signed certificates and servers
that help you to SSL protection. And, CAs stand to reap
the benefits, as do users.
WYTM?
or
What's your threat model?
The threat model is perhaps the most important question
in cryptography. Yet, in the case of SSL and secure browsing,
the question was bungled. The threat model is not only
wrong, in principle and in practice, it has nothing
to do with the original requirements.
The Maginot Web
The CA-signed certificate protects against the
spoof attack on users with all the pomp and circumstance
of the Maginot Line. Huge cost, impeccable theory, and
bypassed in the event.
Who's Afraid of Mallory Wolf?
The dreaded bogey-man has us all afeared, yet, he remains
elusive, fleeting, and like all childhood nightmares,
of exaggerated importance.
Now in
Russian! Thanks to Dani for pointing that out.
How effective is open source crypto?
Extraordinarily so, but the opportunity has been lost.
Yes, these are all rants. Or, at their best,
essays on the lamentable state of SSL security
implementations. It's a complex subject,
and I've been annoyed at certs ever since some
salesman from Cybercash tried to convince me that
I needed them, but couldn't say why.
The "need" for certs - in terms of the way the browsers
force sites to deploy expensive, useless CA-signed
certificates - is still with us. This page seeks to
show that this is a gross failure of security engineering
within the networking world.
But, to do so with yet another boring security paper,
presented at yet another annual conference with too many
acronyms, seems fruitless. Perhaps a more light hearted
approach will reach out? Who knows, you tell me!
Enjoy!
Some of these rants were posted on the
cryptography@metzdowd.com
list, which has a
majordomo subscription.
Archives of the list are stored at
Mail-Archive
(earlier) and at
Mail-Archive
(later)
with responses to some of them at:
For more serious reading, try these:
PKI considered harmful
is a list of issues that exist with the wider scheme
of Public Key Infrastructures.
It has always been an ongoing work-in-progress
over a decade or so, although I've not discovered so
many new issues to add in recent years.
(PS-A4, PDF-A4.)
Browser Threat Model
is an attempt to document the browser threat model,
from today's perspective of 2004.
This was an merely a draft,
thrashed out over a few nights back in 2004. Comments welcome!
See the MindMap of
the secure browsing attack model.
(Also see more recent work from 2009:
Ivan Ristic' blogged on his efforts).
Financial Cryptography entries on Phishing
Since phishing arose to actually challenge the crypto systems
and rip money out of people's online accounts, I've written
quite a lot in more serious forum: the FC blog. Click on
above to see the searched list.
This page is not about actual solutions to Phishing,
but how to solve the underlying bugs that caused phishing.
For solutions to Phishing itself, you are better
off dropping in to the
anti-fraud coffee room.
That being said, here is a list of early research and
experiments in solutions, especially those that have
passed our hypercritical seal of approval.
Curiously, the industry once again moved past the
security aspects of these solutions without noticing,
an observation that led to my thoughts in
The Market in Silver Bullets.
Trustbar
The first and possible most comprehensive approach was
Trustbar!
It is a plugin browser toolbar
that displays the CA's logo and
name, and the domain name of the site.
It also gives the user the ability
to label each site with different
personalised labels.
Petnames
Even simpler yet!
Based on the fundamental concepts of
petnames
and
Zooko's Triangle
the
Petnames toolbar
does one small thing and does it well:
it encourages the user to place a unique personalised label,
or petname, on each important SSL site.
SecuritySkins
This approach tries to create images that the user
knows but are never communicated, derived from a shared secret
approach known as SRP. In some ways it is similar to Trustbar,
in other ways different.
References
[1]
The precise reference for this quote is unknown.
Florian Weimer writes:
Your Popper quote is from a German broadcast program which is reprinted in "Alles Leben ist Problemlösen" (Piper 1994): "Die Amöbe flieht vor der Falsifikation: Ihre Erwartung ist ein Teil von ihr, und vorwissenschaftliche Träger werden oft durch die Widerlegung der Hypothese vernichtet. Einstein dagegen hat seine Hypothese objektiviert. Die Hypothese ist etwas außerhalb von ihm; und der Wissenschaftler kann seine Hypothese durch seine Kritik vernichten, ohne selbst mit ihr zugrunde zu gehen. In der Wissenschaft lassen wir unsere Hypothesen für uns sterben."
So it's more like
"The scientist can annihilate his theory by his critique,
without perishing along with it.
In science, we let our hypotheses die in our stead."
It's a bit distorted, but I still think it's the source of your aphorism
(unless someone discovers a better one).
Twan van der Schoot suggests:
Ref
[2]
R.P. Feynman,
Personal observations on the reliability of the Shuttle
[3]
Ian Stewart,
From What Does a Martian Look Like?
The Science of Extraterrestrial Life

